Phishing Alert: Pay attention to NC State login pages and Duo prompts
In two recent phishing attacks, cybercriminals used fake NC State Shibboleth login pages and fraudulent Duo Security push notifications to trick several members of the campus community into sharing their Unity IDs and passwords.
Fake NC State Login Pages
In these attacks, cybercriminals sent campus IT users an email message that had a PDF attachment with a link to a fake university login page. As shown below, the fake login page appears to be identical to the legitimate Shibboleth login page — except for the URL.
Always make sure the URL of the NC State login page begins with shib.ncsu.edu. If it doesn’t, do not enter your NC State Unity ID or password! While scammers are becoming increasingly clever mimicking the appearance of trusted web pages, they cannot duplicate the beginning of a URL.
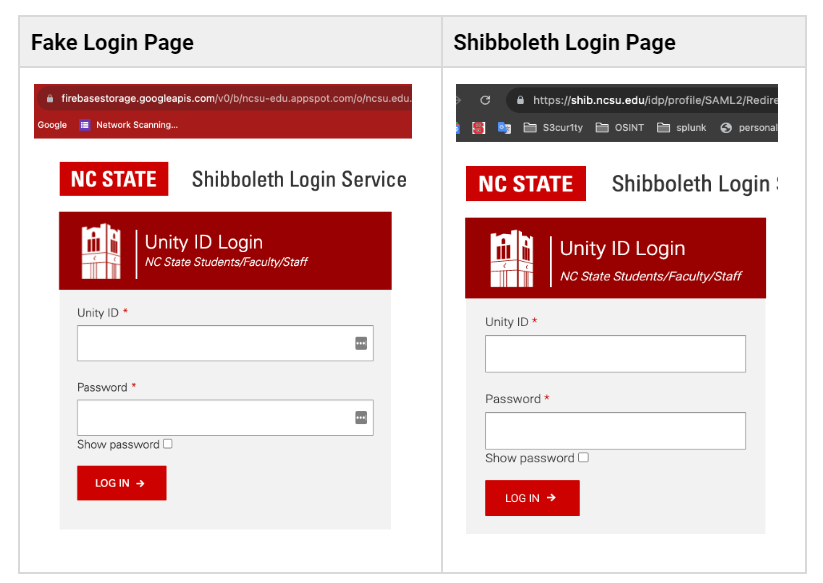
When the unsuspecting users followed the link to the fake login page, they unwittingly shared their Unity IDs and passwords with cybercriminals. The hackers then exploited these credentials to log in to Shibboleth, which then led to a fraudulent Duo push notification being sent to the users’ mobile devices. The users accepted the fraudulent push notification.
Fraudulent Duo Push Notifications
When you receive a push notification from Duo, deny it unless you initiated the login attempt and it matches your expectations.
Cybercriminals are skillfully crafting fraudulent Duo prompts that look legitimate, so take a moment to make sure all Duo notifications:
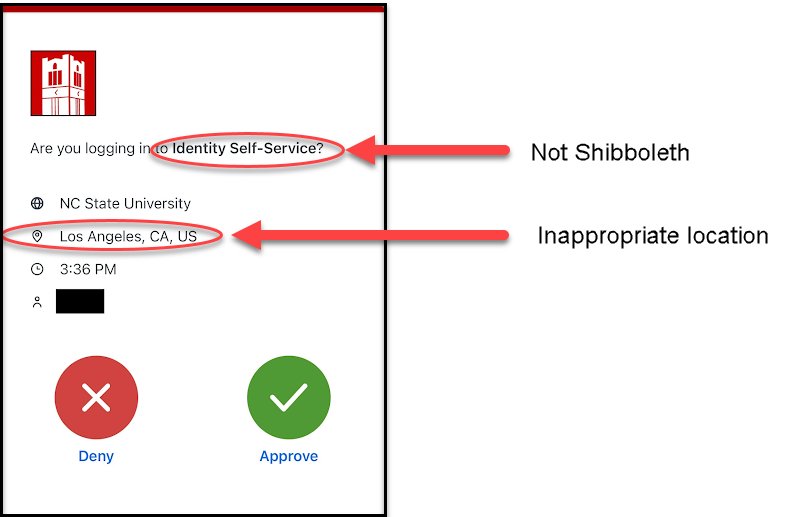
- Indicate NC State University appropriately.
- Match the application or website that you were logging into (Shibboleth versus anything unexpected).
- Match your Unity ID.
- Adequately reflect your Duo access device location.
NOTE: The location (e.g., Raleigh, another city) may vary depending on where you are when logging in — for example, on campus, remote or logged in to the NC State VPN. In some cases, depending on various technical complexities, the location for a legitimate Duo push can be as far away as a neighboring state. So, it can be tricky trying to determine if the Duo location indicates legitimacy or not. But if you’re in Raleigh and the location says Dallas, Los Angeles or a foreign country, you should be suspicious. - Match the time of your attempted login.
- Match origin. For example, you shouldn’t receive a Duo push for “NCSU SSL VPN” when you are not connected to campus via the NC State Virtual Private Network.
As shown below, a fraudulent Duo push notification may provide some red flags to alert you to a phishing attack.
For a demonstration of how to use the Duo push notification, check out the Duo Authenticate with Push Notification video.
If you suspect that you may have used your password on a fake site:
- Change your password immediately.
- Contact your local IT support staff or the NC State Help Desk at 919.515.HELP (4357) or via the NC State IT Service Portal.


