Sidestep MFA Traps

Imagine a robber gets their hands on a key to your house. While you’re out, they stop by to browse your belongings. The robber approaches the front door and unlocks the doorknob. Bingo. Then goes for the deadbolt. Rats. The deadbolt takes a different key.
Multifactor authentication (MFA) is the digital version of that second key. It’s an added layer of security for your accounts that requires you to verify your identity when logging in.
NC State uses Duo Security as its MFA solution. This is an invaluable tool if your password, like your house key, is stolen. But even the best of tools isn’t 100 percent foolproof. Faced with a second security measure, cybercriminals must find new tactics to break through.
Here are a few ways to thwart some common tactics to keep your personal and university data safe.
Download Duo Mobile
Using the Duo Mobile app to verify your identity is more secure than text messages, which are at risk of being intercepted. Through a tactic called SIM swapping, a cybercriminal connects their own SIM card to your phone number — taking control of your calls and texts and potentially stealing your MFA passcodes.
With Duo Mobile, you can securely approve push notifications on your device. Download the app from the App Store or Google Play. After downloading, you must activate your device. See Upgrading to the Duo Mobile App for more information.

Only Approve MFA Requests You Initiated
If you receive an unexpected MFA request, deny it and assume your credentials have been stolen. If you receive numerous, back-to-back push notifications, you are likely caught in an MFA prompt bombing attack. The attacker sends frequent requests in the hopes you will approve one simply to make the notifications stop.
Before approving a Duo Mobile push notification, check that all elements of the request are accurate. This includes reviewing the app or website being logged in to, the physical location of the device, the time of access and the Unity ID. Change your password immediately if you believe it has been compromised.
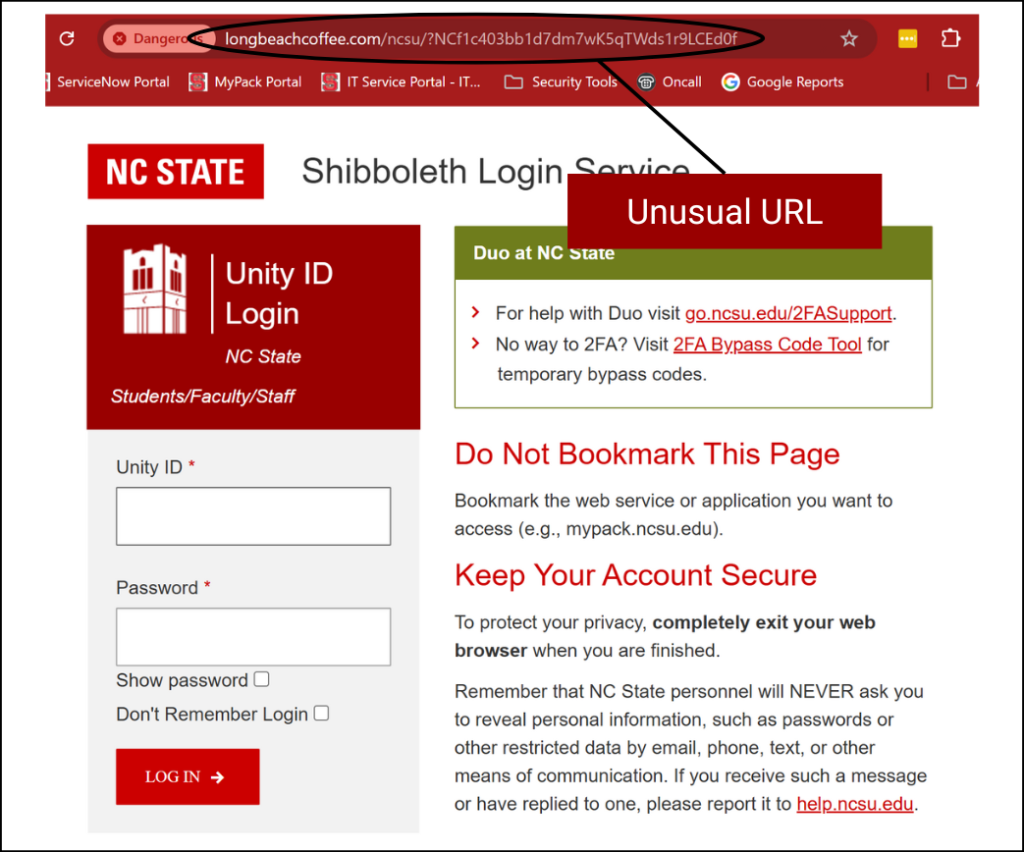
Beware of Look-alike Websites
Fake websites are a popular method for credential theft. This type of phishing is often carried out through a malicious link sent via email or text that sends you to a fake login page. Many NC State students, faculty and staff received a similar phishing scam this spring.
In some scenarios, the cybercriminal simultaneously enters your credentials into the legitimate website, triggering a real MFA request as expected for you to accept. In other scenarios, you may be sent to a second website that resembles an MFA request for a one-time passcode.
Double-check the URL of any website that asks for your personal information, and be on the lookout for anything else that seems abnormal. An NC State login page’s URL will always start with https://shib.ncsu.edu.
As always, remember these three steps to avoid phishing:
- Be suspicious.
- Take your time.
- Ask for help.
For assistance, contact the NC State Help Desk via the NC State IT Service Portal or call 919.515.HELP (4357).
- Categories:


